Architecture – Almaden Agents
Introduction
The Almaden agents are responsible for enabling inventory monitoring of hardware and software, as well as performance and configuration change tracking on Workstations and Servers. It analyzes collected data and presents it in the form of reports. These services are implemented in an internet-centered and automated manner, allowing them to be operated whenever and wherever needed.
The provided services include:
Asset Wizard (Inventory management of hardware, software, and users – User Attributes Form)
Software Metering Wizard (Software usage statistics and executable file tracking)
License Wizard (License usage control)
Distribution Wizard (Distribution of files, commands, and software across multiple machines)
Performance Wizard (Performance and availability analysis)
Capacity Wizard (Capacity planning)
Response Time Wizard (Real-time monitoring and event notifications)
Sizing Wizard (Analysis of stations that meet application requirements)
Components
The service operates with two main components: Web Page (Collective IQ and ITAM) and Collector Agents
Web Page – Collective IQ and ITAM
This page serves as the interface through which users can access and customize Almaden services.
The personal account page is accessed through a secure (SSL) connection, and login can be performed using “username and password” or Azure AD integration.
It provides functions such as:
- Account Administration
- Create and update accounts, acquire new services, request support, etc.
- Download Agents and Documentation
- Download agents for testing or acquisition purposes.
- Download documents such as readme files and manuals.
ADA and ASA – Collector Agents
These components monitor the devices on which they are installed, collecting data about their operation and configuration, encrypting, compressing, and sending it to our servers.
The Agent, used for workstations, operates through the combination of two distinct modules: Agent Module and Relay Module.
The difference between the Desktop Agent (ADA) and the Server Agent (ASA) is the data collection interval:
ASA collects data every minute.
ADA collects data every 60 minutes.
Agent Module
The Agent Module is installed on the device to be monitored. It collects, compresses, and sends the monitored data to the Relay Module. The way information is acquired by the Agent Module is one of the key differentiators of Almaden’ services, as, in most cases, the data is obtained directly from the operating system kernel, significantly reducing system intrusion. In fact, the agents are designed to collect data in the least intrusive way possible for each operating system platform.
Relay Module
The Relay Module receives data from one or multiple Agent Modules, encrypts it, and sends it to Almaden Receiver.
- Each machine’s data package is sent sequentially through the same queue, ensuring data order is maintained.
- The number of connection queues, the maximum and minimum packets per queue, the minimum compression percentage, and the queue verification interval.
The Relay Module can be installed on the same device as the Agent Module, providing the device with the autonomy to communicate directly with our server. If there’s a need to centralize internet transmissions at a single point, the Relay Module can be installed on a separate desktop, which we call the Relay Server. A single Relay Server can centralize and send data from multiple Agent Modules to our server. It is also possible to configure an alternative Relay Server, which is automatically used in case the primary Relay Server fails.
The architecture with separate modules was designed to provide great flexibility in agent installation. The Relay Server acts as a sort of selective proxy for the Almaden service, and can be used to connect isolated networks (for security reasons, for example) with the internet without violating existing security policies. The figures below show the various ways the agents can be implemented.
The diagrams below illustrate the different possible agent implementations:
Img 1 – Agent Module and Relay Module on the same workstation (Sending to the CIQ ITAM cloud.)
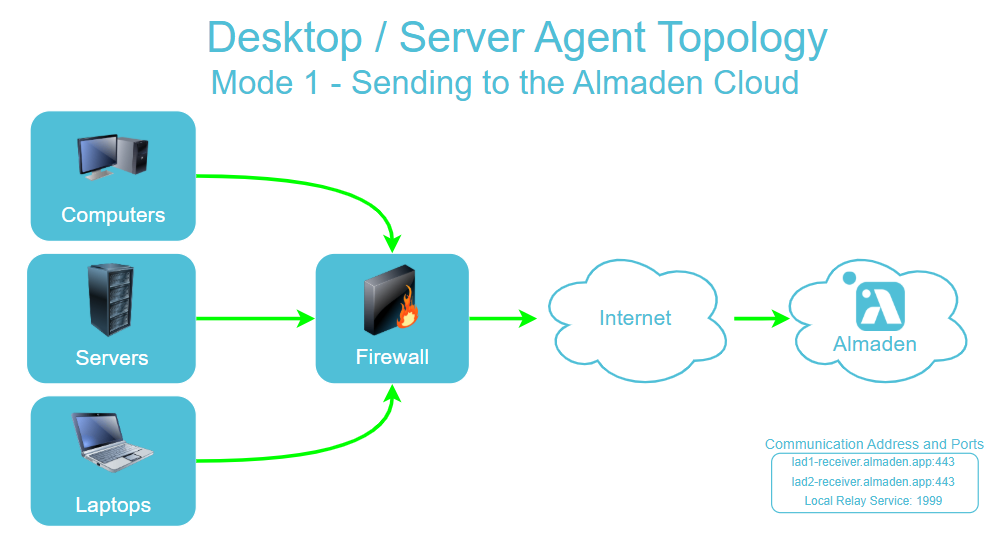
Img 2 – Agent Module and Relay Module on the same device sending data over the internet in case of a Relay failure.
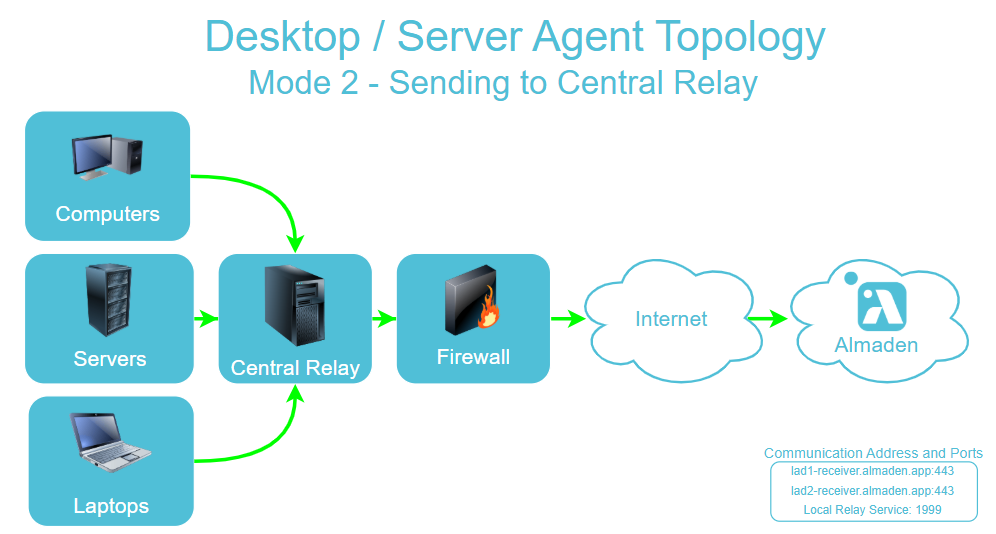
Img 3 – Agent Module without the use of Relay. In this method, we can configure up to 2 centralizing Relay Modules on the same device, ensuring that the data from the workstations does not pass directly through the internet.
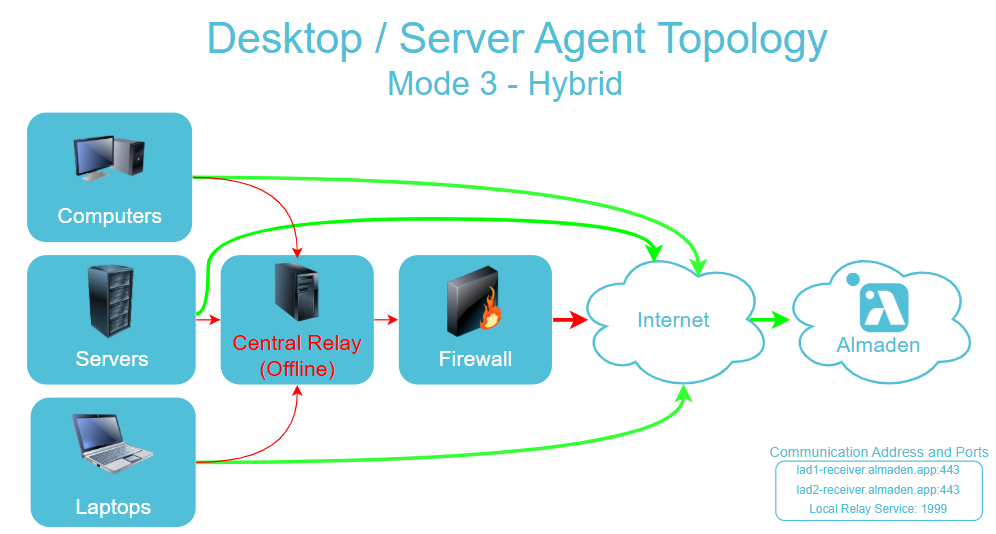
Plugins for the Agent
The collector agents have an open architecture that allows the installation of plug-ins capable of extending an agent’s functionality, enabling it to monitor other performance parameters of a device, such as collecting performance metrics of applications.
Currently, the following plug-ins are available:
Plug-ins installed with the Agents package:
- Asset Plug-in (hardware, software, network, modem, system, monitor, etc inventory)
- Multimedia: Collects information about removable drives of the device.
- RegistryScan: Collects general information via the registry, either for confirmation or retrieval.
- FileDir: Collects file system and executable file paths whose activity has been recorded.
- Group: Collects Windows authentication security groups.
- User: Collects locally or domain-created users who are part of local groups.
- LogInOut: Collects login and logout events.
- Monitor: Collects information about the connected monitor.
- Slotinfo: Collects information about memory slots, what occupies them, and PCI slots.
- Sysinfo: Collects all hardware characteristics of the device.
- Modem: Collects information about modems connected to the device.
- Network: Collects information about the network interfaces of the device.
- Software: Collects information about installed software.
- Capacity Plug-in (inventory and storage monitoring)
- Media: Collects media-related information.
- Performance Plug-in (resource usage monitoring and load planning)
- NetStat: Collects network interface consumption information.
- PsStat: Collects consumption data generated by running processes.
- VmStat: Collects information on processing and memory consumption.
- IoStat: Collects disk performance information.
- Software Metering Plug-in (measuring software and executable usage)
- PowerManager Plug-in (manages energy profile configuration)
Proccess and Services
ADA – Almaden Desktop Agent
It is the main collector agent for desktops. From there, all inventory and performance information is collected and sent to the cloud.
executables: services:
Folder x32 C:\Program Files\Automatos\Desktop Agent\
Folder x64 C:\Program Files (x86)\Automatos\Desktop Agent\
Service: (Almaden) AutomatosDesktopAgent
Service: (Almaden) AutomatosRelay
Executables:
adacontrol.exe
aengine.exe
arelay.exe
enumwindows.exe
epc.exe
ASA – Almaden Server Agent
It is the main collector agent for servers. From there, all inventory and performance information is collected and sent to the cloud.
executables: services:
Folder x32 C:\Program Files\Automatos\Automatos Server Agent\
Folder x64 C:\Program Files (x86)\Automatos\Automatos Server Agent\
Service: (Almaden) AutomatosServerAgent
Service: (Almaden) AutomatosRelay
Executables:
asacontrol.exe
aengine.exe
arelay.exe
enumwindows.exe
epc.exe
ASU – Almaden Software Uninstaller
It is the client that enables the automated removal of software and files using silent and “brute force” methods.
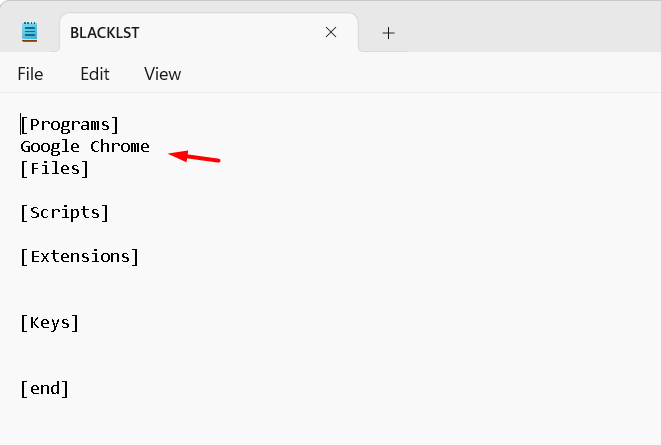
Uninstallation is carried out by reading a script called “Blacklst.ini”.
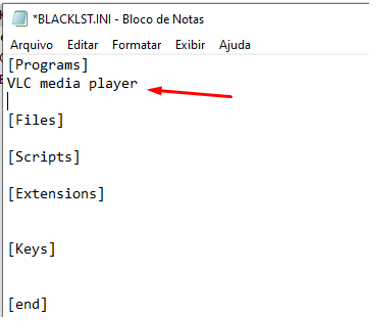
For automatic software removal to work, it is necessary to define which software will be part of the blacklist, that is, software that is not approved in the environment.
Note that in the example image above, the VLC media Player software has been added to the [Programs] tag.
Required files:
When downloading the Almaden Agent, or requesting the installation package from our support, make sure to request or download the complete package (With Software distribution module).
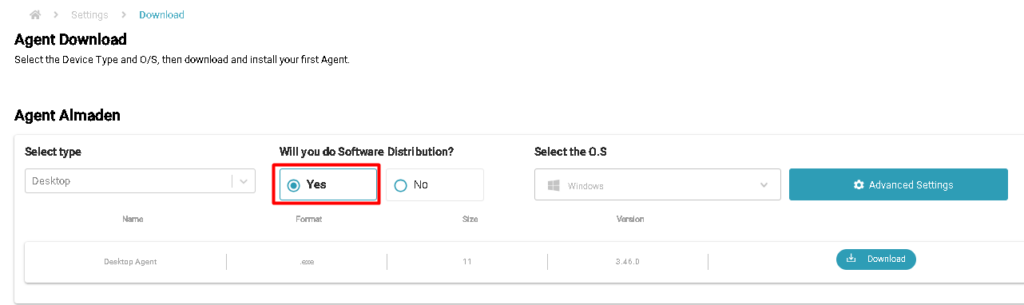
Note: By security standard, these files are not available when installing the Almaden Agent, and you must request them from support by opening a ticket on our ticket portal.
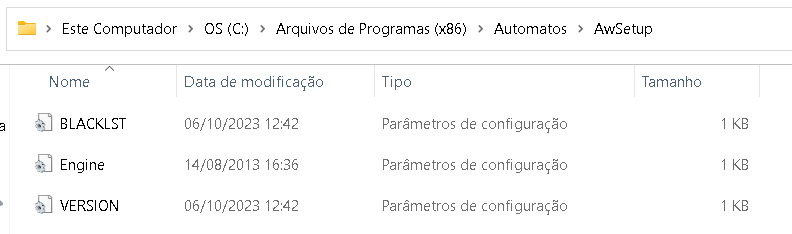
After requesting the necessary files from our support team, save them to the path:
C:\Program Files (x86)\Automatos\AwSetup
Add the name of the programs in the [Programs] tag, according to the Display name, respecting spaces, upper and lower case letters.
Execution time:
The ASU Uninstall Service reads the Blacklist.ini file every time the computer is idle for 1 hour or restarted, removing programs that were added to the list.
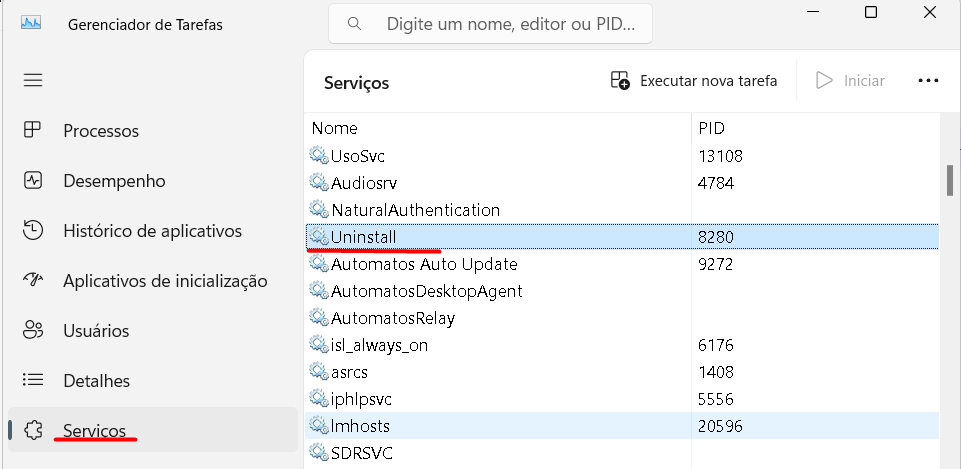
User: “Automatos ASU0”
In assets that have the complete ADA/ASA package installed, that is, the option: “Software distribution modules” was marked when downloading via the CIQ ITAM portal or requested through our ticket portal installation package of the complete Agent, it will contain the ASU service.
When installing this package on computers, the service user will be created: “Automatos ASU0”, to perform software removal when using the black list/ASU.
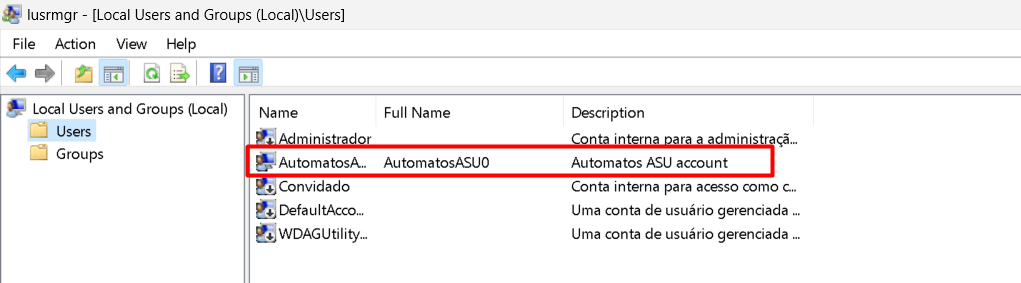
This user is a service user created by the application itself and used only by ASU in the software removal process.
On each computer where this package is installed, the same user will be created but with a different, random password.
When removing the Almaden Agent, using the remover that is compacted to the package, the user will also be removed.
If you do not wish to use ASU, download the package from the CIQ ITAM portal, without selecting the option: “Software distribution modules”, or request the package through our ticket portal, stating that you want the package without the software removal binaries .
For more information about services and executables regarding ASU, visit our prerequisites document.
Automatos Remote Control Server
A remote access application that enables connections to computers running Windows, Linux, and Mac OS. The main features include:
Direct connection using a password: Allows the user to quickly connect to the remote device by entering a password.
Sending invitations via email: The user can send an access invitation to the recipient, which includes instructions to allow the connection.
Sending invitations via link: Alternatively, the user can generate a unique link to facilitate remote access to the device, ensuring convenience and security.
Remote Control Server sends a ping packet to the ISL Conference Proxy server to maintain online status every 30 seconds. There used to be additional packets sent every 5 seconds which were not required. This additional packet sending was removed, and packets are now appended to ping packets, which results in less network traffic.
The ping packet to the server is 131 bytes every 30 seconds to the server, and the server will respond to each ping with the same packet.
Security
Security should be a crucial part of a remote access product, no matter for what purposes you are using it; business or personal
Security Layers
Each connection from a computer to an ISL Conference Proxy server is encrypted with SSL.
ISL AlwaysOn’s activities can be monitored by tracking the history of accesses to a computer. This report shows which ISL Online users accessed the computer and when they accessed it.
A user can always lock access to his/her computer. When disabled, that computer becomes inaccessible until further action.
Layer 1 – ISL Computer visibility
To access a remote computer, it is necessary to establish a link between your account and the target machine. Each user has a digitally signed executable that identifies their account. No other user will be able to view or attempt to establish a remote connection unless the computer administrator has installed the program.
Layer 2 – Computer access password
Whenever the user wants to connect to the remote computer, they will need to enter the access password for each remote access session they initiate.
Layer 3 – MS Windows OS security
Once a user is connected to a remote computer, they will be able to see the Windows console desktop session running on the machine. It is recommended that the user set passwords for all Windows accounts and disable accounts that are not in use. The user should also always log out of the computer when not present, so that when accessing the computer, the Windows account password must be entered.
Internet Connection
The recommended minimum Bandwidth is 56 Kbps.
Bandwidth consumption during audio/video call:
| Video quality and mic/consumption | Network consumption resource manager [kb/s] | Network consumption net balancer [kb/s] |
| Video quality default high | 21,5 | 23 – 62 |
| Video quality default high + mic | 25,5 | 20,5 – 69 |
| Video quality snapshot high | 13,2 | 10 – 12,5 |
| Video quality snapshot medium | 5,8 – 6,2 | 6 – 7 |
| Video quality snapshot low | 5,5 | 5,5 – 6,6 |
| Mic only | 3 – 4,5 | 7 – 8 |
Supported connection methods:
- direct outgoing TCP/IP connection to TCP port 7615 on Conference Proxy server
- WININET HTTPS connection to TCP port 443 on Conference Proxy server
- WININET HTTP connection to TCP port 80 on Conference Proxy server
- direct HTTPS connection to TCP port 443 on Conference Proxy server
- direct HTTP connection to TCP port 80 on Conference Proxy server
Timeout for a specific connection method is 20 seconds for connection establishment – so total timeout for connection is less than 1 minute.
Supported network types:
- A computer with a static public IP
- A computer with a dynamic public IP
- A computer in a private network behind a firewall with a public IP performing NAT
- A computer in a private network behind a http proxy offering http and/or https protocols
Web Browsers
- Firefox
- Google Chrome
- Microsoft Edge
- Microsoft Internet Explorer
- Opera
- Safari
Executable & Proccess
This topic describes executables and processes that are running/started on a computer that has the agent installed and on a computer connecting to it via the Connect client.
Windows
On the remote side (with the agent installed)
AutomatosRemoteControlServerService.exe (watchdog service process – it ensures that the server process is always running)
AutomatosRemoteControlServer.exe (main process that serves functionality)
AutomatosRemoteControlServerTray.exe (tray process is started in each session – it shows the status icon in the system tray)
ISLLightFast.exe (the main ISL Light program that is started by the agent)
MacOS
On the remote side (with the agent installed):
ISL AwaysOn (main process that serves functionality)
ISLAwaysOn Tray (tray process is started in each session – it shows the status icon in the system tray)
Linux
On the remote side (with the agent installed):
ISL AwaysOn service (watchdog service process – it ensures that the server process is always running)
ISL AwaysOn -service-agent (main process that serves functionality)
ISL AwaysOn tray (tray process is started in each session – it shows the status icon in the system tray)

